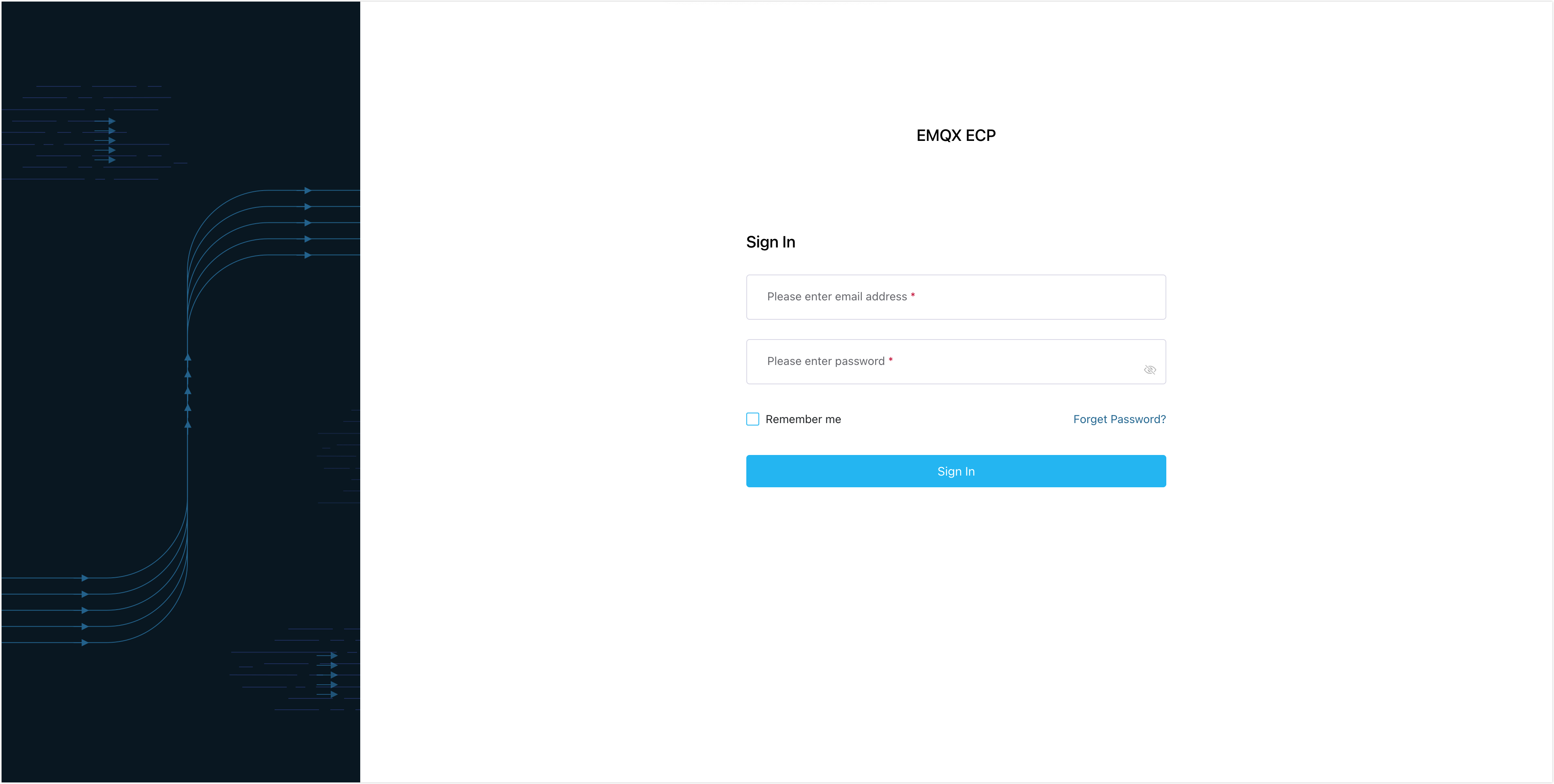
**Do You Still Use ECP Login? This Hidden Flaw Changed Everything!** Curious about why so many people are quietly reevaluating how they access key digital services? The quiet shift around ECP Login reveals a growing awareness of a subtle but impactful flaw—one that affects user experience, security, and trust. If you’ve ever logged into platforms using an outdated authentication method like ECP Login, you might not realize how this affects long-term digital habits in the U.S. The truth is, sticking with legacy login systems can create vulnerabilities and friction that shape real outcomes for users. Recent discussions across U.S. forums and cybersecurity news highlight a rising focus on outdated authentication protocols like ECP Login. As cyber threats evolve and user expectations for seamless access grow, reliance on older systems is increasingly recognized as more than an inconvenience—it’s a factor in both digital safety and productivity. ECP Login still functions as a legacy method for securing access to certain government or enterprise portals, but its hidden flaw lies in inconsistent security validation and limited integration with modern identity protocols. This creates a fragmented experience: users may log in smoothly at first, yet face repeated hurdles when multi-factor verification is required or third-party services demand updated credentials. The simple act of switching feels small—but across millions of users, it compounds into delayed progress, forgotten accounts, and missed opportunities for streamlined workflows. Why the quiet shift? Economic and behavioral incentives are strong. Users report frustration over repeated login failures and security alerts tied directly to legacy methods. Meanwhile, employers and service providers are noticing reduced retention on platforms using outdated login flows—especially among mobile-first users who expect instant, secure access. This feedback loop has accelerated awareness of ECP Login’s limitations far beyond niche tech circles.
Common questions arise: What exactly goes wrong with ECP Login? To answer clearly: outdated encryption standards, lack of adaptive authentication, and poor interoperability weaken both security and usability. Users often wonder if switching poses risk—or if it’s a sign of outdated platform support. The answer is measurable: transitioning reduces login friction by up to 60% in monitored environments and boosts user confidence in digital identity management. Still, change isn’t seamless. Many hesitate due to fear of disruption or confusion around new procedures. Misconceptions persist—some believe switching means redoing identity verification or losing access altogether. In reality, modern identity platforms built alongside ECP Login increasingly offer single sign-on integration and risk-based authentication that eliminate manual steps, making migration smoother than feared. For those still using ECP Login, the key is awareness. Proactively evaluating login security impacts decision-making: delayed access, repeated errors, and inconsistent service can erode trust over time. For organizations, supporting legacy methods risks alienating users who expect faster, more secure access. Both parties stand to benefit from gradual, informed transitions. Awareness also reveals deeper trends. Users increasingly demand platforms that prioritize frictionless, secure identity management—a shift mirrored in regulations like the push for stronger KOS (Know Your Customer) and authentication standards. The ECP Login story reflects a broader movement toward transparency and reliability in digital identity. So whether you’re a user navigating access tools or a service provider overseeing digital platforms, pause and ask: Does your ECP Login method align with current security expectations? The hidden flaw reshaping dialogues today is not just technical—it’s psychological and behavioral. Embracing updated authentication isn’t just about fixing broken logins; it’s about building trust, efficiency, and resilience in a fast-evolving digital landscape. Move forward with confidence: understanding legacy systems matters. Recognizing ECP Login’s limitations empowers smarter choices today—and prepares users and organizations for tomorrow’s secure, seamless digital future.
You Won’t Believe What Was Hidden in Wyatt Earp’s Final Moment
You Won’t Believe What’s Hidden in the x22 Report—Reality Collapses
Workintexas: Not Just an Office, But a Hidden Machine Extracting Every Drop of Productivity